Bonjour,
nouveau portable HP Envy 15-1130ef, windows préinstallé, intel core i7
messages d'erreur de ce type : C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient une erreur. Installez à nouveau le programme à l'aide du support d'installation d'origine, ou bien contactez votre administrateur système ou le fournisseur du logiciel pour obtenir du support
lorsque des exécutables sont lancés, le même problème pour de nombreuses dll : winrnr.dll wshbth.dll rpcrtremote.dll samcli.dll ...
diagnostique : "sfc /scannow"
actions : installation mise à jour windows, outils de diagnostique hp
étonnant ci-dessous : "PROCESSOR_ARCHITECTURE_AMD64"
quelqu'un a une idée ? les dll dépendent du processeur ?
résultat "sfc" ci-dessous :
2011-02-05 22:58:53, Info CSI 00000014 [SR] Cannot repair member file [l:32{16}]"fdrespub.dll.mui" of FDResPub.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:58:55, Info CSI 00000016 [SR] Cannot repair member file [l:34{17}]"IPBusEnum.dll.mui" of IPBusEnum.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:58:55, Info CSI 00000018 [SR] Cannot repair member file [l:32{16}]"fdrespub.dll.mui" of FDResPub.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:58:55, Info CSI 0000001e [SR] Cannot repair member file [l:34{17}]"IPBusEnum.dll.mui" of IPBusEnum.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:21, Info CSI 0000006d [SR] Cannot repair member file [l:26{13}]"csrss.exe.mui" of Microsoft-Windows-Csrss.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:24, Info CSI 0000006f [SR] Cannot repair member file [l:26{13}]"csrss.exe.mui" of Microsoft-Windows-Csrss.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:36, Info CSI 00000088 [SR] Cannot repair member file [l:18{9}]"ehSSO.dll" of Microsoft-Windows-ehome-ehsso, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:38, Info CSI 0000008a [SR] Cannot repair member file [l:18{9}]"ehSSO.dll" of Microsoft-Windows-ehome-ehsso, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:40, Info CSI 00000094 [SR] Cannot repair member file [l:28{14}]"fltmgr.sys.mui" of Microsoft-Windows-filtermanager-core.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 22:59:45, Info CSI 000000c1 [SR] Cannot repair member file [l:28{14}]"fltmgr.sys.mui" of Microsoft-Windows-filtermanager-core.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:01:25, Info CSI 0000014a [SR] Cannot repair member file [l:32{16}]"hidphone.tsp.mui" of Microsoft-Windows-OptionalTSPs.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:01:26, Info CSI 0000014c [SR] Cannot repair member file [l:32{16}]"hidphone.tsp.mui" of Microsoft-Windows-OptionalTSPs.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:01:37, Info CSI 0000015f [SR] Cannot repair member file [l:28{14}]"regsvc.dll.mui" of Microsoft-Windows-RemoteRegistry-Service.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:01:37, Info CSI 00000161 [SR] Cannot repair member file [l:28{14}]"regsvc.dll.mui" of Microsoft-Windows-RemoteRegistry-Service.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:21, Info CSI 00000199 [SR] Cannot repair member file [l:28{14}]"trkwks.dll.mui" of Microsoft-Windows-trkwks.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:21, Info CSI 0000019b [SR] Cannot repair member file [l:32{16}]"upnphost.dll.mui" of Microsoft-Windows-UPnPDeviceHost.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:23, Info CSI 0000019d [SR] Cannot repair member file [l:32{16}]"upnphost.dll.mui" of Microsoft-Windows-UPnPDeviceHost.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:24, Info CSI 000001a3 [SR] Cannot repair member file [l:28{14}]"trkwks.dll.mui" of Microsoft-Windows-trkwks.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:25, Info CSI 000001ad [SR] Cannot repair member file [l:26{13}]"VSSVC.exe.mui" of Microsoft-Windows-VssService.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:29, Info CSI 000001af [SR] Cannot repair member file [l:26{13}]"VSSVC.exe.mui" of Microsoft-Windows-VssService.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:30, Info CSI 000001ba [SR] Cannot repair member file [l:28{14}]"WsmSvc.dll.mui" of Microsoft-Windows-Web-Services-for-Management-Core.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:33, Info CSI 000001bd [SR] Cannot repair member file [l:28{14}]"WsmSvc.dll.mui" of Microsoft-Windows-Web-Services-for-Management-Core.Resources, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:47, Info CSI 000001d5 [SR] Cannot repair member file [l:32{16}]"comctl32.dll.mui" of Microsoft.Windows.Common-Controls.Resources, Version = 6.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope neutral, PublicKeyToken = {l:8 b:6595b64144ccf1df}, Type = [l:10{5}]"win32", TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:02:48, Info CSI 000001d7 [SR] Cannot repair member file [l:32{16}]"comctl32.dll.mui" of Microsoft.Windows.Common-Controls.Resources, Version = 6.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_AMD64 (9), Culture = [l:10{5}]"fr-FR", VersionScope neutral, PublicKeyToken = {l:8 b:6595b64144ccf1df}, Type = [l:10{5}]"win32", TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:03:45, Info CSI 00000225 [SR] Cannot repair member file [l:20{10}]"wshbth.dll" of Microsoft-Windows-BTH-USER, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:03:47, Info CSI 00000227 [SR] Cannot repair member file [l:20{10}]"wshbth.dll" of Microsoft-Windows-BTH-USER, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:11, Info CSI 0000024c [SR] Cannot repair member file [l:32{16}]"wscproxystub.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:11, Info CSI 0000024e [SR] Cannot repair member file [l:24{12}]"wscisvif.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:11, Info CSI 00000250 [SR] Cannot repair member file [l:20{10}]"wscapi.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:12, Info CSI 00000252 [SR] Cannot repair member file [l:32{16}]"wscproxystub.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:12, Info CSI 00000255 [SR] Cannot repair member file [l:24{12}]"wscisvif.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:12, Info CSI 00000258 [SR] Cannot repair member file [l:20{10}]"wscapi.dll" of Microsoft-Windows-SecurityCenter-Core, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:20, Info CSI 00000277 [SR] Cannot repair member file [l:24{12}]"msshooks.dll" of WindowsSearchEngine, Version = 7.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:20, Info CSI 00000279 [SR] Cannot repair member file [l:22{11}]"mssprxy.dll" of WindowsSearchEngine, Version = 7.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:23, Info CSI 0000027e [SR] Cannot repair member file [l:24{12}]"msshooks.dll" of WindowsSearchEngine, Version = 7.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:23, Info CSI 00000281 [SR] Cannot repair member file [l:22{11}]"mssprxy.dll" of WindowsSearchEngine, Version = 7.0.7600.16385, pA = PROCESSOR_ARCHITECTURE_IA32_ON_WIN64 (10), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:30, Info CSI 00000298 [SR] Cannot repair member file [l:22{11}]"dllhost.exe" of Microsoft-Windows-COM-Surrogate, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_INTEL (0), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:32, Info CSI 000002a5 [SR] Cannot repair member file [l:22{11}]"dllhost.exe" of Microsoft-Windows-COM-Surrogate, Version = 6.1.7600.16385, pA = PROCESSOR_ARCHITECTURE_INTEL (0), Culture neutral, VersionScope = 1 nonSxS, PublicKeyToken = {l:8 b:31bf3856ad364e35}, Type neutral, TypeName neutral, PublicKey neutral in the store, hash mismatch
2011-02-05 23:04:38, Info CSI 000002cb [SR] Cannot repair member file [l:20{10}]"samcli.dll" of Microsoft-Windows-Directory-Services-SAM-NetAPI,
...
C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
-
sylvain678
- Messages : 5
- Enregistré le : dim. 6 févr. 2011 13:03
- Etes vous un robot ? : Non
-
Ycor
- Messages : 6459
- Enregistré le : sam. 14 mars 2009 17:30
- Etes vous un robot ? : Non
- Localisation : Lausanne (CH)
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
Bonjour
As-tu installé ou modifié quelque chose juste avant que ces erreurs apparaissent ?
Certains sites référencent RpcRtRemote.dll comme un nuisible :
As-tu installé ou modifié quelque chose juste avant que ces erreurs apparaissent ?
Certains sites référencent RpcRtRemote.dll comme un nuisible :
RpcRtRemote.dll file can be used by hackers to compromise your computer.
I'd want you to follow these steps to remove it from your computer.
Step 1:
To prevent your computer's security and privacy from any risk, you are recommended to run a scan immediately on your computer to detect any spyware threats, or, run an online scan usingthis link.
RpcRtRemote.dll
Step 2: Find RpcRtRemote.dll Path with Windows File Search Tool
1. Click Start, and in the Search box, type in the file name"RpcRtRemote.dll".
2. When Windows search is complete, highlight and right-click on the file "RpcRtRemote.dll" that you want to delete and select "Delete". Alternatively, you can select the file and press the"Delete" button on your keyboard.
You may also stay on the "In Folder" and note down the file path of "RpcRtRemote.dll" on your clipboard, as the file path may be needed to delete RpcRtRemote.dll in the following manual removal steps.
Step 3: Remove RpcRtRemote.dll Processes with Windows Task Manager
1. Press the combination keys CTRL+ALT+DEL or CTRL+SHIFT+ESC to open the Windows Task Manager.
2. Under the tab Processes, search for "RpcRtRemote.dll" process by name from the list of"Image Name".
3. Select the "RpcRtRemote.dll" process and click on the "End Process" button to stop it.
Step 4: Check for and Delete Other RpcRtRemote.dll Files
1. To open the Command Prompt window, click Start and then clickRun; type in cmd and then press the "OK" button.
2. In the emerged window, to change directory, type in "cd name_of_the_folder" (for example, cd C:\Spyware-folder); pressEnter button.
3. Type in "dir /a" and press Enter button to display the folder's content even the hidden files.
4. Once you find the file you're looking for, type in "del name_of_the_file".
Azeez Nadeem - Microsoft Support

En cas de problème constaté sur un sujet, contactez un modérateur par MP. N'intervenez pas vous-même. Merci
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
Bonjour
Pour faire un premier diagnostic, applique les deux propositions ci-dessous.
1- Télécharge et installe Malwarebytes Anti-Malware de RubbeR DuckY
Télécharge et installe Malwarebytes Anti-Malware de RubbeR DuckY
 Double-clique sur le fichier mbam-setup-1.50.exe (sous Vista et 7 autorise les modifications)
Double-clique sur le fichier mbam-setup-1.50.exe (sous Vista et 7 autorise les modifications)
A la fin de l'installation, veille à ce que les options suivantes soient cochées Clique sur Terminer
Clique sur Terminer
Une fenêtre Mise à jour de Malwarebytes' Anti-Malware va s'ouvrir avec une barre de progression.
Puis une autre annonçant le succès de la mise à jour de la base de données. Clique sur OK.
Le programme s'ouvre sur l'onglet Recherche.
Coche Exécuter un examen rapide, clique sur le bouton
Exécuter un examen rapide, clique sur le bouton 
 A la fin du scan, sélectionne tout et clique sur Supprimer la sélection
A la fin du scan, sélectionne tout et clique sur Supprimer la sélection
 Poste le rapport qui s'ouvre après cette suppression.
Poste le rapport qui s'ouvre après cette suppression.
Redémarre le pc si cela est demandé
Tu peux retrouver le rapport dans l'onglet Rapports/Logs avec la date et l'heure d'exécution.
2- Télécharge ZHPDiag de Nicolas Coolman sur ton bureau.
Télécharge ZHPDiag de Nicolas Coolman sur ton bureau.
 Clique sur
Clique sur  pour lancer l'installation.
pour lancer l'installation.
 Clique sur
Clique sur  pour lancer le programme.
pour lancer le programme.
Sous Vista et Sept , il faut cliquer droit dessus et dans le menu contextuel sur Exécuter en tant qu'administrateur.
 Clique sur
Clique sur  pour vérifier si une mise à jour du logiciel est disponible.
pour vérifier si une mise à jour du logiciel est disponible.
 Clique sur
Clique sur  pour lancer le scan.
pour lancer le scan.
 Clique sur
Clique sur  quand le scan sera terminé pour mettre le rapport dans le presse-papier.
quand le scan sera terminé pour mettre le rapport dans le presse-papier.
 Héberge ce dernier sur Cjoint.
Héberge ce dernier sur Cjoint.
Poste le lien obtenu.
 Referme l'outil.
Referme l'outil.
 Le rapport sera enregistré sur le bureau.
Le rapport sera enregistré sur le bureau. 
Si besoin est, nous ferons appel à d'autres outils.
@+
Pour faire un premier diagnostic, applique les deux propositions ci-dessous.
1-
 Télécharge et installe Malwarebytes Anti-Malware de RubbeR DuckY
Télécharge et installe Malwarebytes Anti-Malware de RubbeR DuckY Double-clique sur le fichier mbam-setup-1.50.exe (sous Vista et 7 autorise les modifications)
Double-clique sur le fichier mbam-setup-1.50.exe (sous Vista et 7 autorise les modifications)A la fin de l'installation, veille à ce que les options suivantes soient cochées
- -Mettre à jour Malwarebytes' Anti-Malware
-Exécuter Malwarebytes' Anti-Malware
 Clique sur Terminer
Clique sur TerminerUne fenêtre Mise à jour de Malwarebytes' Anti-Malware va s'ouvrir avec une barre de progression.
Puis une autre annonçant le succès de la mise à jour de la base de données. Clique sur OK.
Le programme s'ouvre sur l'onglet Recherche.
Coche
 Exécuter un examen rapide, clique sur le bouton
Exécuter un examen rapide, clique sur le bouton 
 A la fin du scan, sélectionne tout et clique sur Supprimer la sélection
A la fin du scan, sélectionne tout et clique sur Supprimer la sélection Poste le rapport qui s'ouvre après cette suppression.
Poste le rapport qui s'ouvre après cette suppression.Redémarre le pc si cela est demandé
Tu peux retrouver le rapport dans l'onglet Rapports/Logs avec la date et l'heure d'exécution.
2-
 Télécharge ZHPDiag de Nicolas Coolman sur ton bureau.
Télécharge ZHPDiag de Nicolas Coolman sur ton bureau. Clique sur
Clique sur  pour lancer l'installation.
pour lancer l'installation.  Clique sur
Clique sur  pour lancer le programme.
pour lancer le programme. Sous Vista et Sept , il faut cliquer droit dessus et dans le menu contextuel sur Exécuter en tant qu'administrateur.
 Clique sur
Clique sur  pour vérifier si une mise à jour du logiciel est disponible.
pour vérifier si une mise à jour du logiciel est disponible. Clique sur
Clique sur  pour lancer le scan.
pour lancer le scan. Clique sur
Clique sur  quand le scan sera terminé pour mettre le rapport dans le presse-papier.
quand le scan sera terminé pour mettre le rapport dans le presse-papier. Héberge ce dernier sur Cjoint.
Héberge ce dernier sur Cjoint.Poste le lien obtenu.
 Referme l'outil.
Referme l'outil. Le rapport sera enregistré sur le bureau.
Le rapport sera enregistré sur le bureau. 
Si besoin est, nous ferons appel à d'autres outils.
@+
-
sylvain678
- Messages : 5
- Enregistré le : dim. 6 févr. 2011 13:03
- Etes vous un robot ? : Non
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
Ycor, j'ai constaté les erreurs en démarrant l'assistant "HP Support Assistant" pour commencer, puis sur Adobe Acrobat Reader, ... et suite à l'éxécution de la plupart des exe.
nardino,
execution de ZHPDiaf : même type d'erreur fenêtre "image incorrecte" avec message similaire "C:\Windows\system32\wkscli.dll n'est pas conçu pour s'exécuter ..."
execution de Malwarebytes : aucune erreur, voir le rapport ci-dessous
De plus, j'ai effectué une analyse antivirus Avast => aucun problème
rapport :
Malwarebytes' Anti-Malware 1.50.1.1100
www.malwarebytes.org
Version de la base de données: 5697
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
06/02/2011 23:19:33
mbam-log-2011-02-06 (23-19-33).txt
Type d'examen: Examen rapide
Elément(s) analysé(s): 173106
Temps écoulé: 1 minute(s), 32 seconde(s)
Processus mémoire infecté(s): 0
Module(s) mémoire infecté(s): 0
Clé(s) du Registre infectée(s): 0
Valeur(s) du Registre infectée(s): 0
Elément(s) de données du Registre infecté(s): 0
Dossier(s) infecté(s): 0
Fichier(s) infecté(s): 0
Processus mémoire infecté(s):
(Aucun élément nuisible détecté)
Module(s) mémoire infecté(s):
(Aucun élément nuisible détecté)
Clé(s) du Registre infectée(s):
(Aucun élément nuisible détecté)
Valeur(s) du Registre infectée(s):
(Aucun élément nuisible détecté)
Elément(s) de données du Registre infecté(s):
(Aucun élément nuisible détecté)
Dossier(s) infecté(s):
(Aucun élément nuisible détecté)
Fichier(s) infecté(s):
(Aucun élément nuisible détecté)
nardino,
execution de ZHPDiaf : même type d'erreur fenêtre "image incorrecte" avec message similaire "C:\Windows\system32\wkscli.dll n'est pas conçu pour s'exécuter ..."
execution de Malwarebytes : aucune erreur, voir le rapport ci-dessous
De plus, j'ai effectué une analyse antivirus Avast => aucun problème
rapport :
Malwarebytes' Anti-Malware 1.50.1.1100
www.malwarebytes.org
Version de la base de données: 5697
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
06/02/2011 23:19:33
mbam-log-2011-02-06 (23-19-33).txt
Type d'examen: Examen rapide
Elément(s) analysé(s): 173106
Temps écoulé: 1 minute(s), 32 seconde(s)
Processus mémoire infecté(s): 0
Module(s) mémoire infecté(s): 0
Clé(s) du Registre infectée(s): 0
Valeur(s) du Registre infectée(s): 0
Elément(s) de données du Registre infecté(s): 0
Dossier(s) infecté(s): 0
Fichier(s) infecté(s): 0
Processus mémoire infecté(s):
(Aucun élément nuisible détecté)
Module(s) mémoire infecté(s):
(Aucun élément nuisible détecté)
Clé(s) du Registre infectée(s):
(Aucun élément nuisible détecté)
Valeur(s) du Registre infectée(s):
(Aucun élément nuisible détecté)
Elément(s) de données du Registre infecté(s):
(Aucun élément nuisible détecté)
Dossier(s) infecté(s):
(Aucun élément nuisible détecté)
Fichier(s) infecté(s):
(Aucun élément nuisible détecté)
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
Bonjour
Télécharge avz4.zip de Oleg Zaitzev
Décompresse le fichier sur le bureau dans un dossier du même nom
Double-clique sur AVZ.exe.
Fais une mise à jour du programme en cliquant sur le bouton à droite de la fenêtre.
Clique sur Start pour lancer la mise à jour.
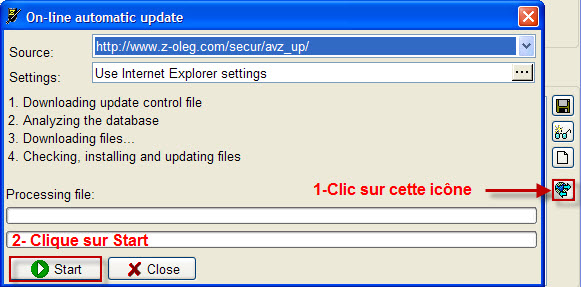
En haut dans le menu File > clique sur Standard Scripts et coche la case "3.Advanced System Analysis whith malware removal mode enabled"
Clique sur Execute selected scripts en bas à gauche.
Clique sur OK à la fin du scan.
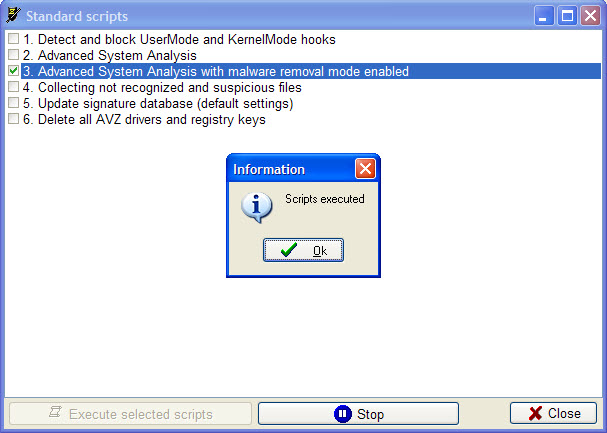
Un fichier/rapport sera créé dans le dossier LOG du dossier AVZ sous le nom virusinfo_syscure.zip.
Il est impératif à ce moment de redémarrer l'ordinateur.
Une fois redémarré, relance AVZ.exe
Toujours dans le menu File > clique sur Standard scripts et coche cette fois la case "2.Advanced System Analysis"
Exécute le script comme ci-dessus.
Un nouveau rapport sera créé avec l'autre sous le nom virusinfo_syscheck.zip
Il n'est utile de redémarrer cette fois.
Poste les deux rapports obtenus dans le sous dossier LOG
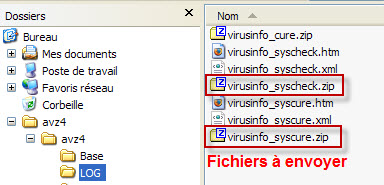
Tu les héberges sur Cjoint et tu postes les deux liens obtenus.
@+
Télécharge avz4.zip de Oleg Zaitzev
Décompresse le fichier sur le bureau dans un dossier du même nom
Double-clique sur AVZ.exe.
Fais une mise à jour du programme en cliquant sur le bouton à droite de la fenêtre.
Clique sur Start pour lancer la mise à jour.

En haut dans le menu File > clique sur Standard Scripts et coche la case "3.Advanced System Analysis whith malware removal mode enabled"
Clique sur Execute selected scripts en bas à gauche.
Clique sur OK à la fin du scan.

Un fichier/rapport sera créé dans le dossier LOG du dossier AVZ sous le nom virusinfo_syscure.zip.
Il est impératif à ce moment de redémarrer l'ordinateur.
Une fois redémarré, relance AVZ.exe
Toujours dans le menu File > clique sur Standard scripts et coche cette fois la case "2.Advanced System Analysis"
Exécute le script comme ci-dessus.
Un nouveau rapport sera créé avec l'autre sous le nom virusinfo_syscheck.zip
Il n'est utile de redémarrer cette fois.
Poste les deux rapports obtenus dans le sous dossier LOG

Tu les héberges sur Cjoint et tu postes les deux liens obtenus.
@+
-
sylvain678
- Messages : 5
- Enregistré le : dim. 6 févr. 2011 13:03
- Etes vous un robot ? : Non
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
nardino, merci pour ton aide
voici ce que ça donne en détail
http://cjoint.com/?0chwKvgrFC4
http://cjoint.com/?0chwLhDDGpH
Ce qui m'etonne le plus :
1)
Direct reading: C:\Documents and Settings\carre\AppData\Local\Application Data\Application Data\Application Data\Application Data\Application Data\Application Data\Application
Data\Application Data\Application Data\Application Data\Temp\~DF499EF7A11A3898F2.TMP
2)
1.1 Searching for user-mode API hooks
Analysis: kernel32.dll, export table found in section .text
Analysis: ntdll.dll, export table found in section .text
Function ntdll.dll:LdrLoadDll (137) intercepted, method - APICodeHijack.JmpTo[64D06946]
Function ntdll.dll:LdrUnloadDll (161) intercepted, method - APICodeHijack.JmpTo[64D069A6]
Function ntdll.dll:NtAllocateVirtualMemory (197) intercepted, method - APICodeHijack.JmpTo[64D069D6]
Function ntdll.dll:NtFreeVirtualMemory (310) intercepted, method - APICodeHijack.JmpTo[64D06AF6]
Function ntdll.dll:NtProtectVirtualMemory (395) intercepted, method - APICodeHijack.JmpTo[64D06BF6]
Function ntdll.dll:ZwAllocateVirtualMemory (1448) intercepted, method - APICodeHijack.JmpTo[64D069D6]
Function ntdll.dll:ZwFreeVirtualMemory (1560) intercepted, method - APICodeHijack.JmpTo[64D06AF6]
Function ntdll.dll:ZwProtectVirtualMemory (1644) intercepted, method - APICodeHijack.JmpTo[64D06BF6]
Analysis: user32.dll, export table found in section .text
Function user32.dll:DefDlgProcA (1657) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F5A->770F8954
Function user32.dll:DefDlgProcW (1658) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F75->770E3F44
Function user32.dll:DefWindowProcA (1664) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F90->770C28B3
Function user32.dll:DefWindowProcW (1665) intercepted, method - ProcAddressHijack.GetProcAddress ->75145FAB->770B243D
Function user32.dll:SetWinEventHook (2216) intercepted, method - APICodeHijack.JmpTo[64D0B716]
Function user32.dll:SetWindowsHookExA (2231) intercepted, method - APICodeHijack.JmpTo[64D0B9A6]
Function user32.dll:SetWindowsHookExW (2232) intercepted, method - APICodeHijack.JmpTo[64D0BB26]
Function user32.dll:UnhookWinEvent (2279) intercepted, method - APICodeHijack.JmpTo[64D0B896]
Function user32.dll:UnhookWindowsHookEx (2281) intercepted, method - APICodeHijack.JmpTo[64D0BCA6]
Analysis: advapi32.dll, export table found in section .text
Function advapi32.dll:AddMandatoryAce (1029) intercepted, method - ProcAddressHijack.GetProcAddress ->762724B5->74D9C334
Function advapi32.dll:I_QueryTagInformation (1361) intercepted, method - ProcAddressHijack.GetProcAddress ->76272655->74E072D8
Function advapi32.dll:I_ScIsSecurityProcess (1362) intercepted, method - ProcAddressHijack.GetProcAddress ->7627268C->74E0733F
Function advapi32.dll:I_ScPnPGetServiceName (1363) intercepted, method - ProcAddressHijack.GetProcAddress ->762726C3->74E07C40
Function advapi32.dll:I_ScQueryServiceConfig (1364) intercepted, method - ProcAddressHijack.GetProcAddress ->762726FA->74E05F8A
Function advapi32.dll:I_ScSendPnPMessage (1365) intercepted, method - ProcAddressHijack.GetProcAddress ->76272732->74E05E7D
Function advapi32.dll:I_ScSendTSMessage (1366) intercepted, method - ProcAddressHijack.GetProcAddress ->76272766->74E071C5
Function advapi32.dll:I_ScValidatePnPService (1369) intercepted, method - ProcAddressHijack.GetProcAddress ->76272799->74E06B9D
Function advapi32.dll:IsValidRelativeSecurityDescriptor (1389) intercepted, method - ProcAddressHijack.GetProcAddress ->762727D1->74D9C5DF
Function advapi32.dll:PerfCreateInstance (1515) intercepted, method - ProcAddressHijack.GetProcAddress ->76272858->74942187
Function advapi32.dll:PerfDecrementULongCounterValue (1516) intercepted, method - ProcAddressHijack.GetProcAddress ->76272871->74942A1D
Function advapi32.dll:PerfDecrementULongLongCounterValue (1517) intercepted, method - ProcAddressHijack.GetProcAddress ->76272896->74942B3C
Function advapi32.dll:PerfDeleteInstance (1519) intercepted, method - ProcAddressHijack.GetProcAddress ->762728BF->74942259
Function advapi32.dll:PerfIncrementULongCounterValue (1522) intercepted, method - ProcAddressHijack.GetProcAddress ->762728D8->749427B9
Function advapi32.dll:PerfIncrementULongLongCounterValue (1523) intercepted, method - ProcAddressHijack.GetProcAddress ->762728FD->749428D6
Function advapi32.dll:PerfQueryInstance (1528) intercepted, method - ProcAddressHijack.GetProcAddress ->76272926->74942373
Function advapi32.dll:PerfSetCounterRefValue (1529) intercepted, method - ProcAddressHijack.GetProcAddress ->7627293E->74942447
Function advapi32.dll:PerfSetCounterSetInfo (1530) intercepted, method - ProcAddressHijack.GetProcAddress ->7627295B->749420B0
Function advapi32.dll:PerfSetULongCounterValue (1531) intercepted, method - ProcAddressHijack.GetProcAddress ->76272977->74942565
Function advapi32.dll:PerfSetULongLongCounterValue (1532) intercepted, method - ProcAddressHijack.GetProcAddress ->76272996->74942680
Function advapi32.dll:PerfStartProvider (1533) intercepted, method - ProcAddressHijack.GetProcAddress ->762729B9->74941FED
Function advapi32.dll:PerfStartProviderEx (1534) intercepted, method - ProcAddressHijack.GetProcAddress ->762729D1->74941F34
Function advapi32.dll:PerfStopProvider (1535) intercepted, method - ProcAddressHijack.GetProcAddress ->762729EB->74942026
Function advapi32.dll:SystemFunction035 (1753) intercepted, method - ProcAddressHijack.GetProcAddress ->76272A3C->72E63EA8
Analysis: ws2_32.dll, export table found in section .text
Analysis: wininet.dll, export table found in section .text
Analysis: rasapi32.dll, export table found in section .text
Analysis: urlmon.dll, export table found in section .text
Library not found netapi32.dll
1.2 Searching for kernel-mode API hooks
Error loading driver - operation interrupted [C000036B]
1.4 Searching for masking processes and drivers
Checking not performed: extended monitoring driver (AVZPM) is not installed
1.5 Checking IRP handlers
Error loading driver - operation interrupted [C000036B]
voici ce que ça donne en détail
http://cjoint.com/?0chwKvgrFC4
http://cjoint.com/?0chwLhDDGpH
Ce qui m'etonne le plus :
1)
Direct reading: C:\Documents and Settings\carre\AppData\Local\Application Data\Application Data\Application Data\Application Data\Application Data\Application Data\Application
Data\Application Data\Application Data\Application Data\Temp\~DF499EF7A11A3898F2.TMP
2)
1.1 Searching for user-mode API hooks
Analysis: kernel32.dll, export table found in section .text
Analysis: ntdll.dll, export table found in section .text
Function ntdll.dll:LdrLoadDll (137) intercepted, method - APICodeHijack.JmpTo[64D06946]
Function ntdll.dll:LdrUnloadDll (161) intercepted, method - APICodeHijack.JmpTo[64D069A6]
Function ntdll.dll:NtAllocateVirtualMemory (197) intercepted, method - APICodeHijack.JmpTo[64D069D6]
Function ntdll.dll:NtFreeVirtualMemory (310) intercepted, method - APICodeHijack.JmpTo[64D06AF6]
Function ntdll.dll:NtProtectVirtualMemory (395) intercepted, method - APICodeHijack.JmpTo[64D06BF6]
Function ntdll.dll:ZwAllocateVirtualMemory (1448) intercepted, method - APICodeHijack.JmpTo[64D069D6]
Function ntdll.dll:ZwFreeVirtualMemory (1560) intercepted, method - APICodeHijack.JmpTo[64D06AF6]
Function ntdll.dll:ZwProtectVirtualMemory (1644) intercepted, method - APICodeHijack.JmpTo[64D06BF6]
Analysis: user32.dll, export table found in section .text
Function user32.dll:DefDlgProcA (1657) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F5A->770F8954
Function user32.dll:DefDlgProcW (1658) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F75->770E3F44
Function user32.dll:DefWindowProcA (1664) intercepted, method - ProcAddressHijack.GetProcAddress ->75145F90->770C28B3
Function user32.dll:DefWindowProcW (1665) intercepted, method - ProcAddressHijack.GetProcAddress ->75145FAB->770B243D
Function user32.dll:SetWinEventHook (2216) intercepted, method - APICodeHijack.JmpTo[64D0B716]
Function user32.dll:SetWindowsHookExA (2231) intercepted, method - APICodeHijack.JmpTo[64D0B9A6]
Function user32.dll:SetWindowsHookExW (2232) intercepted, method - APICodeHijack.JmpTo[64D0BB26]
Function user32.dll:UnhookWinEvent (2279) intercepted, method - APICodeHijack.JmpTo[64D0B896]
Function user32.dll:UnhookWindowsHookEx (2281) intercepted, method - APICodeHijack.JmpTo[64D0BCA6]
Analysis: advapi32.dll, export table found in section .text
Function advapi32.dll:AddMandatoryAce (1029) intercepted, method - ProcAddressHijack.GetProcAddress ->762724B5->74D9C334
Function advapi32.dll:I_QueryTagInformation (1361) intercepted, method - ProcAddressHijack.GetProcAddress ->76272655->74E072D8
Function advapi32.dll:I_ScIsSecurityProcess (1362) intercepted, method - ProcAddressHijack.GetProcAddress ->7627268C->74E0733F
Function advapi32.dll:I_ScPnPGetServiceName (1363) intercepted, method - ProcAddressHijack.GetProcAddress ->762726C3->74E07C40
Function advapi32.dll:I_ScQueryServiceConfig (1364) intercepted, method - ProcAddressHijack.GetProcAddress ->762726FA->74E05F8A
Function advapi32.dll:I_ScSendPnPMessage (1365) intercepted, method - ProcAddressHijack.GetProcAddress ->76272732->74E05E7D
Function advapi32.dll:I_ScSendTSMessage (1366) intercepted, method - ProcAddressHijack.GetProcAddress ->76272766->74E071C5
Function advapi32.dll:I_ScValidatePnPService (1369) intercepted, method - ProcAddressHijack.GetProcAddress ->76272799->74E06B9D
Function advapi32.dll:IsValidRelativeSecurityDescriptor (1389) intercepted, method - ProcAddressHijack.GetProcAddress ->762727D1->74D9C5DF
Function advapi32.dll:PerfCreateInstance (1515) intercepted, method - ProcAddressHijack.GetProcAddress ->76272858->74942187
Function advapi32.dll:PerfDecrementULongCounterValue (1516) intercepted, method - ProcAddressHijack.GetProcAddress ->76272871->74942A1D
Function advapi32.dll:PerfDecrementULongLongCounterValue (1517) intercepted, method - ProcAddressHijack.GetProcAddress ->76272896->74942B3C
Function advapi32.dll:PerfDeleteInstance (1519) intercepted, method - ProcAddressHijack.GetProcAddress ->762728BF->74942259
Function advapi32.dll:PerfIncrementULongCounterValue (1522) intercepted, method - ProcAddressHijack.GetProcAddress ->762728D8->749427B9
Function advapi32.dll:PerfIncrementULongLongCounterValue (1523) intercepted, method - ProcAddressHijack.GetProcAddress ->762728FD->749428D6
Function advapi32.dll:PerfQueryInstance (1528) intercepted, method - ProcAddressHijack.GetProcAddress ->76272926->74942373
Function advapi32.dll:PerfSetCounterRefValue (1529) intercepted, method - ProcAddressHijack.GetProcAddress ->7627293E->74942447
Function advapi32.dll:PerfSetCounterSetInfo (1530) intercepted, method - ProcAddressHijack.GetProcAddress ->7627295B->749420B0
Function advapi32.dll:PerfSetULongCounterValue (1531) intercepted, method - ProcAddressHijack.GetProcAddress ->76272977->74942565
Function advapi32.dll:PerfSetULongLongCounterValue (1532) intercepted, method - ProcAddressHijack.GetProcAddress ->76272996->74942680
Function advapi32.dll:PerfStartProvider (1533) intercepted, method - ProcAddressHijack.GetProcAddress ->762729B9->74941FED
Function advapi32.dll:PerfStartProviderEx (1534) intercepted, method - ProcAddressHijack.GetProcAddress ->762729D1->74941F34
Function advapi32.dll:PerfStopProvider (1535) intercepted, method - ProcAddressHijack.GetProcAddress ->762729EB->74942026
Function advapi32.dll:SystemFunction035 (1753) intercepted, method - ProcAddressHijack.GetProcAddress ->76272A3C->72E63EA8
Analysis: ws2_32.dll, export table found in section .text
Analysis: wininet.dll, export table found in section .text
Analysis: rasapi32.dll, export table found in section .text
Analysis: urlmon.dll, export table found in section .text
Library not found netapi32.dll
1.2 Searching for kernel-mode API hooks
Error loading driver - operation interrupted [C000036B]
1.4 Searching for masking processes and drivers
Checking not performed: extended monitoring driver (AVZPM) is not installed
1.5 Checking IRP handlers
Error loading driver - operation interrupted [C000036B]
-
sylvain678
- Messages : 5
- Enregistré le : dim. 6 févr. 2011 13:03
- Etes vous un robot ? : Non
Re: C:\Windows\system32\RpcRtRemote.dll n'est pas conçu pour s'executer sous Windows ou il contient
Bonsoir,
Merci beaucoup pour votre aide.
Je viens d'effectuer une restauration de mon OS ... après quelques gestes simples qui buggaient auparavant et un nouveau "sfc /scannow" ... tout fonctionne à merveille

Merci beaucoup pour votre aide.
Je viens d'effectuer une restauration de mon OS ... après quelques gestes simples qui buggaient auparavant et un nouveau "sfc /scannow" ... tout fonctionne à merveille
